I was taken a look at some sources showing trends on BI for 2007, especially related to legacy code. I have found interesting the following quotes from a report Knightsbridge Solutions LLC (Trends in Business Intelligence for 2007)
Trend #5
Service-Oriented Architecture: Information Management is Critical to Success (of BI)
The buzz around service-oriented architecture (SOA) continues, with some organizations viewing SOA
as the solution to a wide range of business and technology problems, from improving enterprise agility
to deriving more value from legacy systems (I think we are wintness of that).
In the BI arena, SOA has great potential for delivering
enhanced capabilities to users. An SOA-enabled BI infrastructure could provide seamless access to
both batch and real-time data integrated across operational and analytical sources. SOA also presents
opportunities for innovation in areas such as real-time data collection and real-time analytic services.
However, companies that approach SOA without a strong information management methodology will
have difficulty achieving the benefits they seek. When implementing SOA on a large scale, companies will
face the same barriers they do in large BI integration projects. For example, some early adopters of SOA
found that semantic incompatibilities in the data between disparate systems are a significant impediment
to SOA adoption. These organizations are discovering that master data management and data governance
efforts must precede SOA adoption to provide a “common language” that supports integration. SOA has
the potential to deliver benefits in BI and many other areas, but not without a solid information management
foundation.And also
Trend #8
Influence of Large Vendors: Market Consolidation Expected in 2007
Speculation abounded in 2006 regarding potential acquisitions of pure-play vendors in the BI space.
Business Objects, Cognos, Hyperion, and Informatica were seen as potential acquisition targets with
likely acquirers being enterprise software and infrastructure vendors like IBM, Microsoft, Oracle,
and SAP. Large vendors have moved aggressively into the BI space, building their capabilities through
both acquisitions and internal development (as evidenced by Hewlett-Packard’s recent acquisition
of Knightsbridge).
Strongly consistent with this
http://www.intelligententerprise.com/channels/bi/showArticle.jhtml;jsessionid=ADNU0C0TP01BYQSNDLRSKH0CJUNN2JVN?articleID=199501674
This is also interesting to see in more detail
http://www.spagoworld.org/ecm/faces/public/guest/home/solutions/spago
"Naja" let's see
A quick note – I just noticed I recently went over the
100-post mark here in my blog... yoohoo!! I never thought I would get this far with it. I have to accept that it took me a little over a year to make it, but I finally did it. Hooray!!
Right now my colleague
Stephen is delivering the last hands-on lab of the
Virtualization for Developers Lab Series. This means that one of the most interesting trainings I have delivered is now over. It has been a good run, and, even though we sometimes didn’t get the attendance we wanted, a great experience. Some of the highlights of the series include:
- Meeting all sorts of interesting people with interesting (and crazy) projects at every location
- The experience of getting the setup process for the labs almost fully automated - learned a lot about Windows in the process
- See Windows Server Virtualization live for the first time on a presentation by Arno Mihm at a Redmond event
- Going to a tapas bar (“de tapeo”) in Huesca with some of the attendees at the Zaragoza event
For the next few months we’re going to be working on some new trainings and in some other exciting projects. I’ll keep you all posted. In the meantime, remember about the HP Integrity labs – that’s where I’ll probably head next!
You can specify the rom boot program to use with a specific machine when using WDS. This allows you to set the machines to always try a PXE boot first, and control its behavior from WDS. WDS comes with three x86 boot roms, each with different functionality (this also applies to x64 and Itanium – since I only have x86 machines available for testing, I’ll use those roms):
- Boot\x86\pxeboot.com: Normal boot ROM. It presents the prompt for F12 and boots from WDS ONLY if F12 is pressed
- Boot\x86\pxeboot.n12: Boots directly from the network (PXE) without waiting for F12 to be pressed
- Boot\x86\abortpxe.com: Aborts the PXE boot process and continues booting from the next boot device
In order to change the boot rom, you need to have the machine pre-staged in Active Directory, and use the wdsutil command line program. You also need to know either the name or the MAC address of the machine. With that information, you can issue the command:
wdsutil.exe /set-device /Device:SERVER01 /BootProgram:Boot\x86\pxeboot.n12
OR
wdsutil.exe /set-device /ID:AA-BB-CC-DD-EE-FF /BootProgram:Boot\x86\pxeboot.n12
The previous lines change the boot rom to pxeboot.n12 of the machine SERVER01.
By using this, when you have to restore an image to a machine, you can just change the boot rom to pxeboot.n12, and the process will take place automatically (depending on how you have it configured). Once it is restored, you can change it back to abortpxe.com, and it will continue booting from the hard drive every time.
Sometimes
negative experiences may turn out positive in the long-run, everybody should
hope to believe in whenever things do not happen the way we expected. Though already
old, maybe questionable and controversial, I must realize this speech made me reflect a
lot about it, I found it very rich in philosophical material; it changed me
somehow. If you haven’t yet, you could find interesting to watch it
Video: http://www.youtube.com/watch?v=D1R-jKKp3NA
Text: http://news-service.stanford.edu/news/2005/june15/jobs-061505.html
Next month we’ll be at the last planned HP Integrity Developer Workshop, in East Rutherford, NJ, between June 12-14. We’ll be in charge of the Windows 64–bit track.
This is the last workshop planned for this year, so make sure you take this opportunity to get hands-on training with HP’s Integrity Servers using Dual-core Itanium CPUs. You can choose to receive training in either Windows, Linux, HP/UX or OpenVMS, and get help with your ports to the Itanium platform. Plus you get to take back home the server you worked on! Check out the benefits from the class (from the Workshop Overview):
- your dual-core Itanium-based application porting efforts well underway or in many cases, completed.
- The HP Integrity rx2620 server that you used in the classroom sent directly to you from the workshop for your continued porting and testing efforts.
- free software development tools
- membership in HP's Developer & Solution Partner Program that allows you to take advantage of GTM and lead generation programs once your port is completed.
Make sure you reserve your spot for the workshop!
There are a list of situations you might want to handle with Active Directory:
525 - user not found
52e - invalid credentials
530 - not permitted to logon at this time
532 - password expired
533 - account disabled
701 - account expired
773 - user must reset password
This is an extract of the Java Forum to handle these cases. Good Luck!
} catch (AuthenticationException e) {String tempString;
StringTokenizer tokenizerTemp = new StringTokenizer(e.toString());
while (tokenizerTemp.hasMoreElements()) { tempString = tokenizerTemp.nextToken();
if (tempString.equalsIgnoreCase("AcceptSecurityContext")) { while (tokenizerTemp.hasMoreElements()) { tempString = tokenizerTemp.nextToken();
if (tempString.startsWith("773")) setIsPasswordExpired(true);
if (tempString.startsWith("52e")) setIsPasswordWrong(true);
if (tempString.startsWith("533")) setIsAccountDisabled(true);
}
}
}
throw new NamingException();
}
It is common that after a migration to Java, specially coming from legacy platforms like LINC or COBOL, that our clients want to take advantage of new technologies. So it happens that they are now authenticating against an Active Directory or another LDAP server. And thanks to the new platforms it is really easy for us to help them integrate this new functionality.
This is sample program that show how to authenticate with for example a Windows Active Directory.
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.util.Hashtable;
import javax.naming.Context;
import javax.naming.NamingEnumeration;
import javax.naming.NamingException;
import javax.naming.directory.Attributes;
import javax.naming.directory.SearchControls;
import javax.naming.directory.SearchResult;
import javax.naming.ldap.InitialLdapContext;
import javax.naming.ldap.LdapContext;
public class LDAPTest
{
static class LDAP
{
static String ATTRIBUTE_FOR_USER = "sAMAccountName";
public Attributes authenticateUser(String username, String password, String _domain, String host, String dn)
{
String returnedAtts[] ={ "sn", "givenName", "mail" };
String searchFilter = "(&(objectClass=user)(" + ATTRIBUTE_FOR_USER + "=" + username + "))";
//Create the search controls
SearchControls searchCtls = new SearchControls();
searchCtls.setReturningAttributes(returnedAtts);
//Specify the search scope
searchCtls.setSearchScope(SearchControls.SUBTREE_SCOPE);
String searchBase = dn;
Hashtable environment = new Hashtable();
environment.put(Context.INITIAL_CONTEXT_FACTORY, "com.sun.jndi.ldap.LdapCtxFactory");
//Using starndard Port, check your instalation
environment.put(Context.PROVIDER_URL, "ldap://" + host + ":389");
environment.put(Context.SECURITY_AUTHENTICATION, "simple");
environment.put(Context.SECURITY_PRINCIPAL, username + "@" + _domain);
environment.put(Context.SECURITY_CREDENTIALS, password);
LdapContext ctxGC = null;
try
{
ctxGC = new InitialLdapContext(environment, null);
// Search for objects in the GC using the filter
NamingEnumeration answer = ctxGC.search(searchBase, searchFilter, searchCtls);
while (answer.hasMoreElements())
{
SearchResult sr = (SearchResult)answer.next();
Attributes attrs = sr.getAttributes();
if (attrs != null)
{
return attrs;
}
}
}
catch (NamingException e)
{
System.out.println("Just reporting error");
e.printStackTrace();
}
return null;
}
}
public static void main(String[] args) throws Exception
{
InputStreamReader converter = new InputStreamReader(System.in);
BufferedReader in = new BufferedReader(converter);
System.out.println("Please type username:");
String username = in.readLine();
System.out.println("Please type password:");
String password = in.readLine();
LDAP ldap = new LDAP();
//Yo specify in the authenticate user the attributes that you want returned
//Some companies use standard attributes like 'description' to hold an employee ID
//The ActiveDirectory data can be enhanced to add custom attributes like
//printer
// Some instalations usually have several ACtiveDirectoryServers, lets say
// 192.150.0.8, 192.150.0.7 y 192.150.0.9 and they use a
// DNS round robin to balance the load
Attributes att = ldap.authenticateUser(username, password, "mydomain.com", "myactivedirectoryhost.com", "DC=mydomain,DC=com");
if (att == null)
{
System.out.println("Sorry your use is invalid or password incorrect");
}
else
{
String s = att.get("givenName").toString();
System.out.println("GIVEN NAME=" + s);
}
}
}
Just wanted to share a nice
tool I found to create quick links at blog posts. Developed by Laurence Gonzalves using the Google AJAX Search API, this is perfect for those constant bloggers who make extensive use of hyperlink tags.
Today I finally got a chance to play with Beta 2 of the System Center Virtual Machine Manager. Here are my preliminary impressions:
- First of all, the product has improved significantly. It has tons of new features, and uses tons of new pre-requisites. Fortunately, you can download a pre-configured VHD with SCVMM, ready to go, from Microsoft Connect.
- This version of SCVMM uses the new Windows Remote Management (WinRM) package to manage remote servers. This is a step in the right direction, IMHO, since it is Microsoft’s implementation of the WS-Management Protocol. The downside is that I had to install the WinRM package on the servers, but well, its a nice trade-off for getting a SOAP-based, standard management product.
- One thing I really like about it is the Powershell integration. It is finally included in this version of SCVMM, and the implementation rocks – at the end of most wizard, you get a button that says “View Powershell Script”:

Pressing that button shows you the Powershell script equivalent to the options you selected:
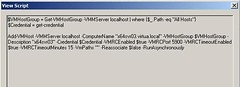
So far I’ve only been able to add hosts and manage the virtual machines on those hosts. I am looking forward to working with the new advanced features, including (and especially) the physical to virtual migration. Overall I think the new features are great, and you should give it a try.
This is small Example. I had a POS Application in VB6 with this code.
Me.EpsonFPHostControl1.SendCommand
While EpsonFPHostControl1.State = EFP_S_Busy
DoEvents
Wend
This code is almost the same in VB.NET
Me.AxEpsonFPHostControl1.SendCommand()
While AxEpsonFPHostControl1.CtlState = EpsonFPHostControlX.TxFiscalState.EFP_S_Busy
Application.DoEvents()
End While
POS (Point of Sale) software is everywhere. Whether you're at a Bar, at Denny's, Pizza Hut, BK or at the Duty Free. It is maybe one of the software's more commonly used. A POS system is generally simple. It manages a basic inventory, registers sales, and somethings manages credit card payments. Obviously there are far more complex POS systems. A lot of POS systems where programmed in VB6. But as you know VB6 language (and I'm not discussing the reasons here) is now a dead language. A lot of customers do not want to buy VB6 applications, even if they get the job done. So it's time to move on. This is the First of a series of posts around issues migrating VB6 POS applications. If you have any comments just send them now!
I was developing a WebPart and I came up with a situation where my custom ToolPart did not fired the events.
I found this post that solved the problem.
"
I moved the databinding code into the CreateChildControls()
code:
protected override void CreateChildControls()
{
dllCatagory = new DropDownList();
dllCatagory.Visible = true;
dllCatagory.AutoPostBack = true;
dllCatagory.Attributes.Add("runat", "server");
dllCatagory.SelectedIndexChanged += new
EventHandler(dllCatagory_SelectedIndexChanged);
CdCatagoryList.CatagoryList cdCatL;
cdCatL = new CdCatagoryList.CatagoryList();
//cdCat.Catlist is a dll that will get the data.
DataView tviewFolders = cdCatL.CatList(true, "cdadmin", "",
"server=192.168.221.246;uid=DataSa;pwd=pa456;database=ContentDepot");
dllCatagory.DataSource = tviewFolders;
dllCatagory.DataValueField = "FolderNumber";
dllCatagory.DataTextField = "FolderName";
dllCatagory.DataBind();
Controls.Add(dllCatagory);
}
public void dllCatagory_SelectedIndexChanged(object sender, EventArgs e)
{
//Code to load the gridview
//This event now fires}
protected override void RenderToolPart(HtmlTextWriter output)
{
EnsureChildControls();
dllCatagory.RenderControl(output);
}
"
We are racing against time to get an application ready that needs to deploy images with WDS and Active Directory. This is the latest problem I have encountered:
Ok, so based on this article (http://technet2.microsoft.com/windowsserver/en/library/383538a3-4129-4205-b363-d36b08e22ca81033.mspx?mfr=true)
, when using WDS and having the machine boot, you can bypass the F12
keypress by replacing pxeboot.ini by pxeboot.n12. This works like a
charm, all machines that boot into the PXE server bypass the F12 key.
However, I would like to specify which machines should boot fron
pxeboot.com and pxeboot.n12. I generated an Excel sheet that has the
info required to prestage the client on the AD. This is what I have
entered on the 4th row:
SERVER01 GUID Location.... \\wds_server_name\reminst\Boot\x86\pxeboot.n12
This
pre-stages the machine on AD and based on what I have read, will point
the machine (identified by its GUID to boot from the pxeboot.n12 file).
I have used the script called "PrestagRISCInt.vbs" (found here: http://www.microsoft.com/downloads/details.aspx?familyid=aaf0a7a4-71c1-4ee9-b974-66214651a23b&displaylang=en) and issued the following command:
cscript /InputFile:C:\Foo.xls /Server:hpc-dc
After a short wait, I get the following message: "Success creating new computer accounts in Active Directory based on UUIDs!"
When I boot tha machine, it still requests F12 to be pressed, which means that it is STILL using pxeboot.com to boot.
I have followed all the instructions carefully, any idea on what the problem might be?
I recently had a situacion where I needed to extract images from a word document. This can be cumbersome, tedious and you can loose the fidelity of your images
I found two good aproaches: first see
Approach One. This approach indicates to save the document as a web page.
In my case I needed images with a sequence I could follow. Like Figure1 Figure2 etc and I needed them with the best quality possible. So I used another link recommended
Approach Two which has a macro that you can use to export your image as bmp.
Those two links were of great help to me. I recommended them.
While looking for a way to fully automate the installation of wim image file to a server, we immediately stumbled upon a small problem. When doing a PXE boot, the boot rom imaged asked for the F12 key to be pressed. If the key was not pressed, the machine booted normally into Windows - so much for the automation idea, huh?
Fear not, as Stephen sent me a link that explains the following from a RIS installation:
"...To enable a fully automated RIS-based installation, it is necessary to substitute the Startrom.n12 boot file for the default Startrom.com boot file..."
Further reading revealed this vital piece of information:
To configure all clients serviced by a RIS server with an automated installation, rename the startup boot files as follows:
• Change Startrom.com to Startrom.bak
• Change Startrom.n12 to Startrom.com
These files are located in the following directory location on your RIS server:
RemoteInstall\OSChooser\i386
There are certain differences between the RIS and WDS installations, but nothing big. First off, the location of the files for boot time (given that it is a 32-bit box is the following):
\\WDS_Server_Name\reminst\Boot\x86
There you will not find Startom.com and Startrom.n12, but rather pxeboot.com and pxeboot.n12.
If you rename pxeboot.n12 to pxeboot.com, your machine will PXE boot and will NOT ask for F12 key press. Ok, now that the problem is solved, we can go back and try to find solutions for the remaining 500.
Source IP for connected applications in DB2
Usually when there are performance problems you need to
track who is connected to the database. Especially in development environments
because production environments are more restricted with who has access to the
DB.
You can easily list the applications connected to your DB2
database using the control center application or from the command line.
From the control center:
- First
check that the Objects Detail Pane is active
- In the
Objects Details Pane, click the application list link
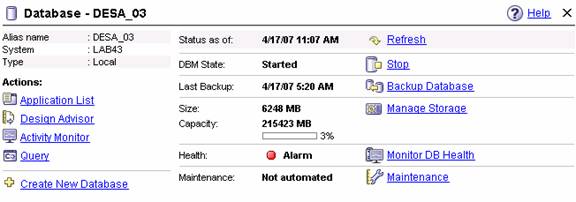
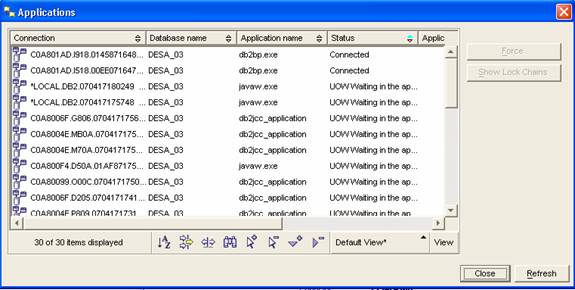
- This
will open a window like this:
From the command window just do something like:
DB2 LIST APPLICATIONS
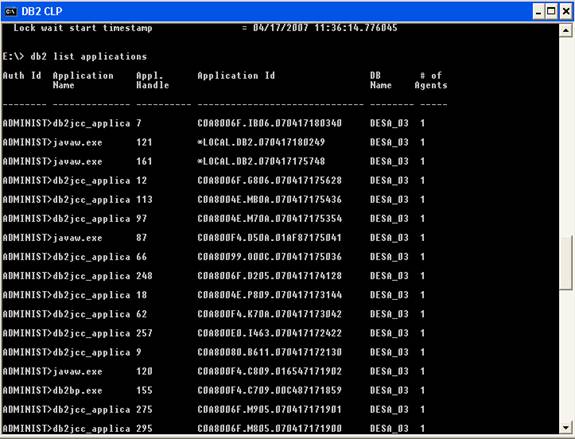
Now to get the real juicy and useful information execute
from the command line:
DB2 GET SNAPSHOT FOR APPLICATION AGENTID ###
And use the number that is under the Appl.
Handle column, this will show the ip address and
other info.
On a previous post I was having problems with the VMRC ActiveX control when creating an instance at runtime. The problem boiled down in having an invalid OCX state exception thrown at me whenever I tried to access a property of the VMRC ActiveX control at runtime.
After researching for quite a while on the Internet, it struck me that if I just placed the VMRC ActiveX in a UserControl at Design time, and instantiated that UserControl instead of the ActiveX directly, things would work great. I implemented this into the VMCA application and it worked perfectly fine. You can see I managed to get VMRC connections to different machines in different tabs at runtime on this post.
Some people have asked where they can get a copy of the VMCA. Unfortunately as of now, the application hasn't been thoroughly tested and is missing some functionality which I deem as basic. Also, this is something I have been working on my spare time and lately I have been swamped with other projects. Perhaps the best approach would be to take it to stable phase and then try and get it on CodePlex so that everyone can pitch in...we'll see how that goes.
For all things related to software migration, be sure to visit Artinsoft's website. For training in Visual Basic to C# migrations, Visual Basic to VB.Net, Virtualization, and 64-bit training check our training web page.
This past two weeks I have been working on a deployment that involves technologies like PXE, WinPE, Windows Deployment Services, the Windows Automated Installation Kit, and others. I was stuck for a while with WinPE, having issues when trying to capture a Windows image using the WDS Capture disk.
Most of the issues I had were driver-related. When I started, neither the network nor the hard drive of the machine (SATA drivers!! argh!!) were available to WinPE.
So, I did the following:
- Get the storage drivers from Intel’s website. You can download them from here. Make sure you download the Vista version of the drivers.
- Unpack them on a temporary directory. In my case I ran:
iata621_enu.exe -A -PF:\intel
- Mount the Capture WinPE 2.0 wim image (generated through the WDS console) to a directory:
imagex /mountrw d:\temp\capture.wim 1 d:\temp\wpe
- Copy the file C:\Program Files\Windows AIK\Tools\x86\imagex.exe to d:\temp\wpe or where you mounted the wim image).
- Now, add the drivers to the WinPE image with the following command:
peimg PF:\intel\*.inf d:\temp\wpe\Windows
- Unmount the WinPE wim image:
imagex /unmount /commit d:\temp\wpe
- Add the WIM image to WDS. On the console, select Windows Deployment Services->Servers->->Boot Images->(Right Click)->Add Boot Image, and browse to the WIM you just unmounted
- Boot the target machine using PXE and make sure it loads the correct WIM image
- Ok, so here is where I had issues:
- First, the WDS Image Capture Wizard didn't list the SATA drives. Turns out the driver loaded correctly, but for some reason it couldn't see the drive.
- If you run into an issue where the driver won't load, try using the drvload command from the WinPE command prompt..
- Because of those issues, I had to fall back to the command line. To do this, press Shift-F10 in the Capture Wizard, and that will open a command prompt.
- Once in the command prompt, create the image using imagex:
imagex /capture c: c:\myimage.wim "My Image" /compress maximum
- With the image created, map a network drive on the server, and copy it back:
net use i: \\\share * /user:
- Copy the image back to the server (I: drive)
- Turn the machine off.
- Enjoy your newly captured image!!!!
Today Microsoft released the Beta 2 of Carmine System Center Virtual Machine Manager. This Beta 2 release adds long-awaited functionality, like P2V and V2V migration, among others. From the release notes:
- Completely new look-and-feel (same as System Center Operations Manager 2007, Service Desk and System Center Essentials)
- Physical-to-Virtual (P2V) Conversions
- Virtual-to-Virtual (V2V) Conversions
- 64-bit VMM server support
- EveryVMM component is now remotely installable
- Full Windows PowerShell support
- Better overall performance and scalability
- Every feature from Beta 1 with more functionality and enhancements
I am currently downloading it, and will post back once I get a chance to play with it a little bit. One of the features that I’m dying to try out is the Powershell support – as powerful as vbscript is, I’m not particularly fond of it, and replacing its use on yet another MS product is another step in the right direction.
You can download Beta 2 from https://connect.microsoft.com/vmm. Remember you have to register first!