Microsoft and ArtinSoft published the Upgrade guide for Visual Basic 6 to .NET. This guide is been re-purposed as a list of FAQs to easily search and allow programmers and managers to find out about the best practices when planning a migration project from VB to Visual Basic .NET 2005.
The first two chapters are out, more will come in the next weeks.
"The purpose of these pages is to provide a comprehensive FAQ for the Upgrading Visual Basic 6.0 to Visual Basic .NET and Visual Basic 2005 guide. This VB migration material was developed jointly by Microsoft and ArtinSoft, a company with vast experience in Visual Basic conversions and the developer of the Visual Basic Upgrade Wizard, the Visual Basic 6.0 Upgrade Assessment Tool, the Visual Basic Upgrade Companion and the ASP to ASP Migration Assistant, among other software migration products."
Link to Upgrading VB6 to .NET – migration guide FAQ
The other day I heard a joke about project managers told by John Valera, one of the Project Management professors at Costa Rica's Universidad Nacional, so I wanted to share it in this space. I’m not really good at telling jokes, but here it goes…
There was a big project which had three key team members: a software architect, a QA leader and a project manager. These three guys used to go together for a walk after lunch, to relax and talk about the project. One day, they came across an old lamp and when they picked it up, a genie appeared and said:
- “You have awaken me. I’m supposed to grant you three wishes, but since you are three, I will grant a wish to each one of you”.
First, the QA leader said:
- “I wish to flee to some place where I can have all the money that I want, and spend it in whatever I want!” Suddenly, he disappeared and became a rich man in Las Vegas.
Then came the software architect:
- “I wish to flee to some place where I don’t have to worry about anything, and I can have all the fun in the world!” Suddenly, he disappeared and found himself walking in the beautiful beaches of Rio de Janeiro.
At the end, it was the project manager’s turn. With no need for extra thinking, he just said:
- “I wish to have those two guys back at work by 2:00 PM!!!!” :)
Sample Code to Print in Java
import
java.io.ByteArrayInputStream;
import javax.print.Doc;
import javax.print.DocFlavor;
import javax.print.DocPrintJob;
import javax.print.PrintService;
import javax.print.PrintServiceLookup;
import javax.print.SimpleDoc;
import javax.print.attribute.HashPrintRequestAttributeSet;
import javax.print.attribute.PrintRequestAttributeSet;
public
class Class3 {
static String textToPrint = "Richard North Patterson's masterful portrayals of law and politics at the apex of power have made him one of our most important\n" +
"writers of popular fiction. Combining a compelling narrative, exhaustive research, and a sophisticated grasp of contemporary\n" +
"society, his bestselling novels bring explosive social problems to vivid life through characters who are richly imagined and\n" +
"intensely real. Now in Balance of Power Patterson confronts one of America's most inflammatory issues-the terrible toll of gun\n" +
"violence.\n\n" +
"President Kerry Kilcannon and his fiancée, television journalist Lara Costello, have at last decided to marry. But their wedding\n" +
"is followed by a massacre of innocents in a lethal burst of gunfire, challenging their marriage and his presidency in ways so shattering\n" +
"and indelibly personal that Kilcannon vows to eradicate gun violence and crush the most powerful lobby in Washington-the Sons of\n" +
"the Second Amendment (SSA).\n\n" +
"Allied with the President's most determined rival, the resourceful and relentless Senate Majority Leader Frank Fasano, the SSA\n" +
"declares all-out war on Kerry Kilcannon, deploying its arsenal of money, intimidation, and secret dealings to eviscerate Kilcannon's\n" +
"crusade and, it hopes, destroy his presidency. This ignites a high-stakes game of politics and legal maneuvering in the Senate,\n" +
"the courtroom, and across the country, which the charismatic but untested young President is determined to win at any cost. But in\n" +
"the incendiary clash over gun violence and gun rights, the cost to both Kilcannons may be even higher than he imagined.\n\n" +
"And others in the crossfire may also pay the price: the idealistic lawyer who has taken on the gun industry; the embattled CEO\n" +
"of America's leading gun maker; the war-hero senator caught between conflicting ambitions; the female senator whose career is at\n" +
"risk; and the grief-stricken young woman fighting to emerge from the shadow of her sister, the First Lady.\n\n" +
"The insidious ways money corrodes democracy and corrupts elected officials . . . the visceral debate between gun-rights and\n" +
"gun-control advocates . . . the bitter legal conflict between gun companies and the victims of gun violence . . . a\n" +
"ratings-driven media that both manipulates and is manipulated - Richard North Patterson weaves these engrossing themes into an\n" +
"epic novel that moves us with its force, passion, and authority.";
public static void main(String[] args) {
DocFlavor flavor = DocFlavor.INPUT_STREAM.
AUTOSENSE;
PrintRequestAttributeSet aset =
new HashPrintRequestAttributeSet();
/* locate a print service that can handle it */
PrintService[] pservices = PrintServiceLookup.lookupPrintServices(flavor, aset);
/* create a print job for the chosen service */
int printnbr = 1;
DocPrintJob pj = pservices[printnbr].createPrintJob();
try {
/* * Create a Doc object to hold the print data.
* Since the data is postscript located in a disk file,
* an input stream needs to be obtained
* BasicDoc is a useful implementation that will if requested
* close the stream when printing is completed.
*/
ByteArrayInputStream fis =
new ByteArrayInputStream(textToPrint.getBytes());
Doc doc =
new SimpleDoc(fis, flavor, null);
/* print the doc as specified */
pj.print(doc, aset);
}
catch (Exception ex){
ex.printStackTrace();
}
}}
TIP: If you are just testing create a Printer. Just go to Add Printers, select FILE for port and Manufacturer Generic and TEXT Only
Today I decided to test out the Volume Shadow Copy (VSS) support in Virtual Server 2005 R2. In theory, as I mentioned in an earlier post, with VSS, virtual server can create a consistent “snapshot” of a running virtual machine so other applications, such as backup clients, can use that snapshot without interrupting the virtual machine itself.
The only VSS-aware backup application I had installed was Windows’ very own NTBackup. So, I enabled VSS on the volumes, run NTBackup, and proceed to make a backup of my virtual machine. Everything started out OK, until NTBackup got stuck with the message “Waiting to retry shadow copy…”. Following my standard error-solving checklist, I checked the Event Viewer, and I found this message logged:
Volume Shadow Copy Service error: Error calling a routine on the Shadow Copy Provider {f5dbcc43-b847-494e-8083-f030501da611}. Routine details BeginPrepareSnapshot({f5dbcc43-b847-494e-8083-f030501da611},\\?\Volume{0cb1b616-8ea6-11db-88de-806e6f6e6963}\) [hr = 0x80070002].
We use Acronis imaging solution for deploying our server, and it turns out that Acronis’ VSS Provider has an issue with Microsoft’s VSS provider. Apparently the issue is well-known, and is documented in two forums posts. It is solved in the latest version of Acronis’ products, but I didn’t really had time to perform an upgrade (and Acronis’ products are notoriously stubborn when you try to uninstall them). So, I applied the solution suggested in one of the forum posts. I unregistered Acronis’ VSS provider using the command:
regsvr32 /u \windows\system32\snapapivss.dll
After that, the backup went without problems:
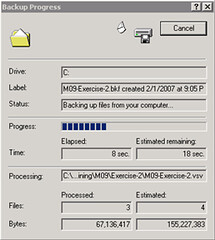
Opening up the log once the backup is complete shows you that all files from the virtual machine were backed up succesfully:
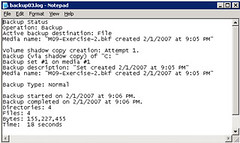
This was done without turning the virtual machine off, taking advantage of the VSS functionality in Virtual Server 2005 R2 SP1 Beta. I performed the same operation on a Windows XP box, disabling NTBackup’s VSS support, and the backup predictably failed.
Here’s some information on VSS: Volume Shadow Copy Service (VSS)
We continue our regular series of
posts talking about refactoring of Web Pages based on semantic approaches; we
invite the interested new reader to take a look at the previous contributions
to get a general picture of our intentions.
In this particular and brief post,
we just want to present and describe some simple but interesting empirical data
which are related with the structural (syntactic) content of some given muster
of pages we have been analyzing during the last days. The results are part of a
white page we are preparing, currently; it will be available at this site in
short time.
We may remember from our first
post that we may want to recover semantics from structure given particular clues
and patterns we usually may come across when analyzing pages. The approach is
simpler to describe than to put into practice: Once semantics could be somehow detected,
refactoring steps can be applied on some places at the page and, by doing so, some
expected benefits can be gained.
However, syntactic structure is
the result of encoding some specific semantics and intentions on a web page
using HTML elements and functionality; the HTML language is (expressively
speaking) rather limited (where too much emphasis on presentation issues is the
case, for instance) and some common programming “bad practices” increase the
complexity of recovering semantics mainly based on syntactic content as input.
And being HTML quite declarative, such complexity can make the discovering
problem quite challenging in a pragmatic context, indeed. That is our more
general goal, however, we do not want to go that far in this post, we just want
to keep this perspective in mind and give the reader some insight and data to
think about it. We will be elaborating more on recovering in forthcoming posts.
As usual in NLP field, it is
interesting to use the so-called Noisy-Channel model as point of reference and
analogy. We may think of the initial semantics as the input message to the
channel (the programmer); the web page is the output message. The programmer
uses syntactic rules to encode semantics during coding adding more or less noisy
elements. Different encodings forms do normally exist, noisy can be greater
when too much structure is engaged for expressing some piece of the message.
A typical example of noisy
encoding is the use of tables for handling style, presentation or layout
purposes beyond the hypothetically primary intention of such kind of table
element: just to be an arrange of data. Complex software maintenance and sometimes
lower performance may be a consequence of too much noise, among others matters.
Let us take a look at some data
concerning questions like: how much noise in page? What kind of noise? What
kind of regular encodings could be found?
As a warning, we do not claim
anything on statistical significance because our muster is clearly too small
and was based on biased selection criteria. Our results are very preliminary,
in general. However, we feel they may be sound and believable, in some way
consistent with the noisy model.
Our “corpus” comes from of 834
pages which were crawled starting for convenience at a given root page in Costa Rica,
namely: http://www.casapres.go.cr/. The size depended of a predetermined
maximal quantity of 1000 nodes to visit; we never took more than 50 paths of
those pointed in a page and we rather preferred visiting homepages to avoid
traps.
Let us see some descriptive profile
of the data. For current limitations of the publishing tool, we are not
presenting some charts complementing the raw numbers.
Just 108 kinds of tags were
detected and we have 523.016 instances of them in corpus. That means, very
roughly, 6 kinds of tags per page, 627 instances per page. We feel that suggests the
use of the same tags for saying probably different things (we remark that many
pages are homepages for choice).
The top 10 of tags are: pure text,
a, td, tr, br, div, li, img, p and font (according to absolute frequency). Together
text, a (anchor) and img correspond to more than 60% all instances. Hence 60%
of pages are some form of data.
We notice that ‘table’ is 1% and
td 8.5% of all instances, against 42% from text, 15% from anchors. In average,
we have 7 tables per page and 54 tds per page, 6 td per table, roughly
speaking.
Likewise we just saw 198
attributes and 545.585 instances of attributes. The 10 most popular are: href,
shape, colspan, rowspan, class, width, clear and height, which is relatively consistent
with the observed tag frequency (egg. href for anchor, colspan and rowspan for
td).
We pay some special attention to
tables in the following lines. Our corpus has 5501 tables. It is worth to
mention that 65% of them are children of td; in other words nested into another
table. Hence a high proportion of nesting which suggests complexity in table
design. We see that 77% of data (text, a, img) in muster are dominated by tds
(most of the data is table dominated). In the case of anchors, 33% of them are
td-dominated, what may suggest tables being used as navigational bars or similar semantic
devices in an apparently very interesting proportion.
We decided to explore semantic
pattern on tables a little bit more exactly. For instance, we choose tables of nx1
dimension (n rows, 1 column) which are good candidates for navigational bars. A
simple analysis shows that 618 tables (11%) have such a shape. The shape may be
different which is quite interesting. For instance, we see a 5x1 table where all td
are anchors. We denote that but a sequence of 1 and 0, where 1 means the
corresponding td contains an anchor (a link to some url): in this case ‘1.1.1.1.1’
is the sequence. But another table of the same 5x1 size presents the pattern ‘1.0.1.0.1’.
This same pattern occurs several times for instance in 50x1 table. Another case
is this: ‘0.0.0.0.1.1.1.1.1.0’ maybe suggesting that some
links are not available. We mention that 212 patterns are 1x1, which would be a
kind of navigation button. We will present more elaborated analysis of this
table patterns in the following post.
To finish, we notice that 875 tables (16%) are not regular:
some rows have different size. Some of them are very unusual like in this 28x8
table, where each number in following sequence denotes the size id tds of the
row: 4.4.4.6.8.8.7.2.8.4.4.6.6.6.6.5.4.5.5.5.5.5.5.5.5.5.5.1.
Noisy, isn’t it?
End users are sometimes ignored when planning a migration project. Traditional software development methodologies often lack an appropriate level of involvement from the end user, and this can limit end-user satisfaction with the final product. Before you begin a migration, it is important that you understand the needs of the users of the original application: after all, they are the ones who will use the migrated application in their everyday activities. Be sure to gather the following information on the perception that end users have on the original application:
-
Features that the users dislike: sometimes the users consider that certain features of the original application are not suited to their needs, or should be improved. If this is the case, you will be migrating something that the users don’t like, so you can expect the same disapproval when you finish the migration. Because of this, it’s a good idea to make the necessary improvements after you reach Functional Equivalence on the target platform. On certain cases, rewriting those particular features or modules can be a good option too.
-
Features that the users depend on: in several applications, you will find that there are features the users can’t live without, and even the slightest change of functionality could cause a problem. For example, in a data-entry form that is designed for fast-typing users entering lots of information, something as simple as changing the TabOrder of the form controls could be disastrous.
Of course this list is not exhaustive, so be sure to involve the end users form the beginning of the project and gather enough information from them. Whenever possible, make their needs part of the requirements for the migration or the post-migration phases.
Este viernes termina nuestro segundo sprint, que empezó a un tanto abruptamente hace dos lunes. ¿Qué pasó? Érase el martes de la primer semana del que originalmente era el segundo sprint, cuando apareció en nuestro Outlook un tímido mail de QM contando que acababa de salir un nuevo release de PR. ¿Qué es PR? Un producto que en un principio parecía ser un acérrimo competidor, después cambiamos el rumbo con un buen diferenciador...¡y de repente salen con una versión que parece una copia de nuestro Product Backlog! Emergencia, gritos, llantos y la crisis que es oportunidad. Miércoles reunión a las corridas con ZF y AC. Baraja que te baraja alternativas y decidimos volver a reunirnos el jueves, que también resultó a puro debate. Ya pasado el mediodía decidimos apretar el botón rojo: abnormal sprint termination. El viernes lo usamos para preparar entre todos algunas User Stories y el lunes siguiente, a correr. A ver qué nos depara el Review del 2/2...
All of you are probably aware that you can download MSDN Pre-Configured Virtual Machine Images and of configurations you can get with the VHD Test Drive. There is another option, though, if you want to evaluate a Windows 2003 R2 installation by itself on a virtual machine or as a host for Virtual Server 2005 R2. You can get a 180–day evaluation of Windows 2003 Server R2 at the trial software page over at Microsoft. This makes it easier to evaluate the performance of the server product, for virtualization, or for any other tasks that you may be considering it.
Link: Windows Server 2003 R2: How to Get Trial Software
There are many many alternatives out there that will assist you to migrate a Physical machine to a Virtual - heck, even NT Backup can be used to accomplish this. The supported procedure recommended to carry out this procedure is to use ADS to create an image of the source machine and then dump it to a Virtual Machine. I am currently testing this procedure and trust me, it is not a straightforward one.
Given the choice, I would recommend any other approach when carrying out a P2V migration. VMWare currently released they migration utility that allows to move physical machines to virtual ones. It even goes the extra mile and imports various virtual machines from other solutions such as Microsoft's Virtual Server.
This is perfect for users of VMWare, but what about if you want to carry a P2V migration to the Virtual Server format? Well, you can still carry this out by using VMWare's tool and then using this utility to convert from VMWare to Virtual Server format. Not the cleanest solution, but I guess this is a perfect example in which the ends justify the means ;)
Como dije, mucho no voy a contar, aunque cuente mucho. Llamemos al proyecto en el que estamos embarcados
CC. El nosotros ya es, como la realidad, complejo de describir: quien suscribe cumple el rol de ScrumMaster,
ZF es Product Owner y el Equipo lo integran, por ahora y solamente por ahora,
AD,
MC y
MR. Estamos trabajando en conseguir por lo menos 5 personas más. Además está
AC, que participa del lado del Product Owner, aunque no puede dedicar mucho tiempo al proyecto. Y además
LC, que va a integrar un equipo aparte, que va a tomar tareas de investigación. Y
QM, que del dominio sabe un montón. Y
SL, que está con temas de marketing. Pero en lo que a mí respecta todos estos últimos no son más que stakeholders. Importantes, cruciales, pero siguen siendo
chickens.
El objetivo es poder tener un beta "lo antes posible". La idea es salir con la versión 1.0 a mediados de año. Como creo haber contado antes, lo que tenemos entre manos es un producto masivo. Lo que se dice software enlatado, aunque la imagen evoque conservas o duraznos en almíbar. El lugar de trabajo por ahora son las oficinas de Sabana Norte, aunque en breve nos vamos a estar mudando a la zona este, por Curridabat. Por ahora tenemos algo bastante parecido a un "team room" (belicosamente conocido también como "war room"), del que espero poder postear algunas fotos en breve. Para realizar el tracking de product backlog items y tareas estamos usando básicamente post-its y papelitos. Estamos probando hacer iteraciones de 2 semanas de duración. El Daily Meeting se hace todos los días a las 13:30hs y está durando unos 8 minutos más o menos. El Sprint Planning Meeting está timeboxeado en 2 horas (1 hora con el Product Owner y 1 hora solamente para el equipo), el Sprint Review Meeting en 1 hora y la Retrospectiva también en 1 hora. Para las llegadas tarde al Daily Meeting tenemos una cajita que usamos de alcancía y que bautizamos "el chanchito". Mandé a comprar un cronómetro para las reuniones de lo más chulo.
(suspiro)...creo que con esos datos ya se pueden ir ubicando...
La idea de este blog va a ser contar esos detalles nimios que colorean todo proyecto de desarrollo. Y no es cualquier proyecto, sino que este va a puro primerizo: mi primer proyecto como ScrumMaster y el primero utilizando Scrum en Artinsoft. Qué puedo decir? Basicamente todo aquello que no puedo. En principio voy a contar poco y nada sobre el producto en si. Lo segundo es más polémico: nombres. Voy a usar iniciales para referirme al resto de los integrantes del grupo de trabajo. Pero esí, chismosos del mundo, a no ilusionarse. La idea no es sacar trapitos al sol, sino simplemente dejar asentado qué pasa en esta oficina...si puedo, día por día.
Product Managers are among the most important --and influencing stakeholders in a migration project. Actually, they are the “owners” of the application that is being migrated and because of this, they may be reluctant to approve changes to the application.
In many cases, it will not be possible to reach the state of Functional Equivalence in a target platform with 100% the same user interface features as the original application. For example, Tab Controls in Visual Basic 6.0 don’t respond to click events when they are disabled, so the user cannot see the contents of the tab. In Visual Basic .NET, tab controls still respond to click events when they are disabled, so they display their contents in a disabled state. This visual difference is intrinsic to the way the .NET control behaves, and therefore it should be regarded as an expected change after the migration.
Just like the one I mentioned, there may be several changes in the application as part of the migration process. It is very important to make Product Managers aware of these expected changes, and have their approval before the changes are made. Product Managers will have great degree of influence on your migration project, so do your best to keep them on your side!
Before I get started on this blog post, allow me to say that this is something that you should never do in a production environment. That being said, when working with the Administrative Web Interface of Virtual Server, it will prompt you for username/password when you start the browser session and when you want to use VMRC to control a VM:
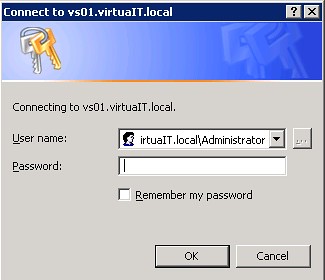
See that "Remember my password" checkbox? Well, it has never worked for us, and according to David Wang, this is an issue with the Virtual Server's Administrative Web Interface being accessed not as an Intranet site but rather as an Internet site. I tried messing with the security settings of my trusted site to allow the use of the currently logged on user on the sites - this lead me nowhere as the web site would not even show up.
I then proceeded to mess with some settings with IIS and I have achieved my purpose: no more password input every time I need to VMRC! . It is worth mentioning again that this is something I am doing on an isolated machine that we use for testing purposes - never, ever do this on a production machine!!!
Here is what you need to do:
- Access the IIS Control Panel
- Expand the following nodes: Virtual Server --> VirtualServer
- Right click on the VirtualServer node and select Properties
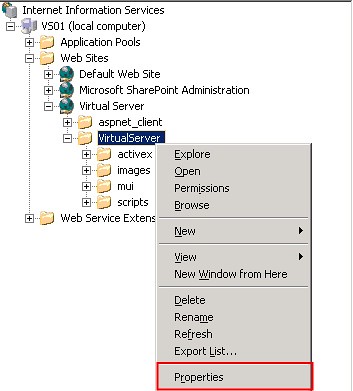
- Click on the Directory Security Tab
- Click the Edit button under Authentication and access control
- Mark the check labeled "Enable anonymous access"
- Enter a username/password combination that is allowed to access Virtual Server
So far what you have done will allow you to access Virtual Servers main Administrative interface. If you want to skip the whole username/password issue when using VMRC, you must change some settings in IE:
- Access Internet Options from within IE
- Select the Trusted Sites Zone
- Click on Custom level
- Scroll all the way to the bottom and under User Authentication--> Logon, select "Automatic logon with current user name and password"
- Close the dialogs, restart IE
Once you do this, you will be able to access the Administrative Web Interface as the user you specified above. Nifty trick for testing but a big no-no for any other scenario.
The first step is to download the actual VM Additions. You can read more about the Linux VM Additions here. To download the additions, you need to log into Microsoft Connect, and the look in the available programs for the Virtual Machine Additions for Linux. Once you download and install the file VMAdditionsForLinux32Bit.MSI, you will have an additional ISO file under C:\Program Files\Microsoft Virtual Server\Virtual Machine Additions\, called VMAdditionsForLinux.iso. This ISO file will appear on the Known image files on the virtual machine’s CD/DVD Drive properties:
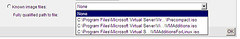
Once you mount the ISO, installing the additions is straightforward. You only need to change the directory to the CD-ROM drive from a terminal (in this case, /media/cdrom), and run the script vmadd-install.run. This script takes several parameters, depending on what part of the additions you wish to install. You can, for example, only install the SCSI driver, or the X11 driver, or any other component. I installed all of them using the command line ./vmadd-install.run all:
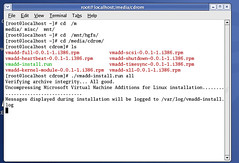
You can also install the additions using the RPM packages, if your distro supports it. Once the additions were installed, the VM worked like a charm. The mouse integration works perfectly, and the performance increase is noticeable.
As suggested in this post by Christian, I went ahead and downloaded the vmdk2vhd utility to convert virtual hard drives from VMWare’s VMDK format to Microsoft’s VHD format. To test it out, I also downloaded Red Hat Enterprise Linux trial virtual appliance from VMWare’s site, and ran the converter on it. These are my results.
First, running the converter is pretty straightforward. You just launch the utility, and it presents you with a simple UI, where you select the vmdk you want to convert, and the path to the destination VHD.
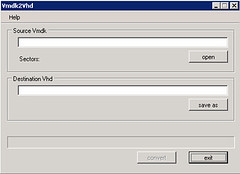
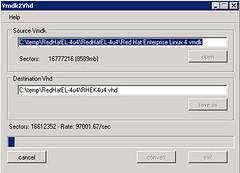
Once you select the vmdk and the vhd, press the convert button to start the conversion process:
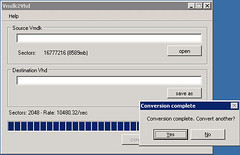
The tool shows you a dialog box when it completes the conversion:
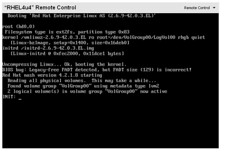
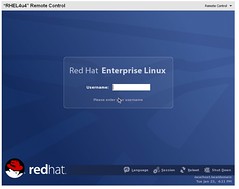
I created a new virtual machine in Virtual Server 2005 R2 SP1 Beta 2 using this newly converted VHD, and, not knowing what to expect, I started it. The redhat OS started the boot up process normally:
After making some adjustments to the configuration, including the X Server configuration, I finally got the X Windows server to come up. I am currently playing with the OS, and will proceed to install the VM Additions … I will document the process in another post soon.
As you can see, the process for converting a VMWare virtual hard disk to a Virtual Server VHd is very straightforward. This will work, ideally, in a migration scenario, but this also enables a scenario to try out the large amount of Virtual Appliances that you can download from VMWare’s website.
Virtual Server 2005 R2 SP1 Beta 2 includes VHD offline mounting, which can be very useful to read the contents of a virtual hard drive from the host, without having to load a virtual machine to do the job.
It might be useful from time to time for some people to have the same feature for Virtual Floppy Disks (.vfd) files. Just to give you an example, some tools depend on floppy disks to create backups that you may be interested on accessing from a physical machine.
This feature is not available with Virtual Server and it probably won't be (I don't think Microsoft would consider this a priority). But if you ever happen to need this, Ken Kato has created a Virtual Floppy Driver that you can use. It lets you view, edit, rename, delete or create files on a virtual floppy disk.
If you browse around the site you will also find a lot of VMWare tools that you might find useful.
If the tasks that your application carries out are independent of each other, a way to optimize things is to create threads for various tasks. There are many ways to thread applications including Pthreads, windows threading, and recently OpenMP. OpenMP excels in the sense that it can make your application multi-threaded by just writing a few pragmas here and there.
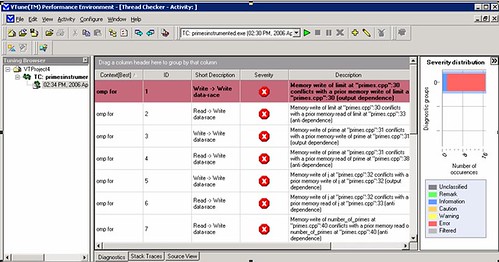
Once you multi-thread your application, many things can go astray. For instance, different threads can access variables at different intervals in a loop, which can only lead to disastrous results in your calculations. You can break your head and lose some of your sanity by manually debugging what is going wrong with your application or you can use Intel's thread checker to find out what is going on. For instance, the following sceenshot shows you the output of all the problems (referred to as data races) when various threads were accessing variables and changing them on each loop:
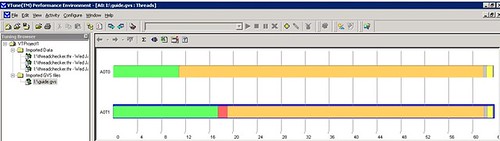
Furthermore, your application's threads might starve waiting for a particular resource to be freed, which can only make the whole multi-threading effort futile. Tools like Intel's thread profiler can help you find this info. For example, after data collection, based on the following screenshot, you can pretty much tell that due to locks in the code, the threads are pretty much stalling the application:
Now that you know what these two tools are and what they do, what I wanted to show you was how to get around the fact that none of these tools can be installed on a Itanium box. That is, now that the Itanium is dual-core, how do you go about optimizing multi-threaded apps using these tools? The solution to this problem will be included in the second part of this post, stay tuned!
The idea was to create a harry potter like title jeje.
Today I had a new issue with DB2 (everyday you learn something new).
I got to work and we had some tables that you could not query or do anything. The system reported something like:
SQL0668N Operation not allowed for reason code "1" on table "MYSCHEMA.MYTABLE".
SQLSTATE=57016
So I started looking what is an 57016 code????
After some googling I found that the table was in an "unavailable state". OK!!
But how did it got there? Well that I still I'm not certain. And the most important. How do I get it out of that state?????
Well I found that the magic spell is somehting like
>db2 set integrity for myschema.mytable immediate checked
After that statement everything works like a charm.
DB2 Docs state that:
"Consider the statement:
SET INTEGRITY FOR T IMMEDIATE CHECKED
Situations in which the system will require a full refresh, or will check the whole table
for integrity (the INCREMENTAL option cannot be specified) are:
- When new constraints have been added to T itself
- When a LOAD REPLACE operation against T, it parents, or its underlying tables has taken place
- When the NOT LOGGED INITIALLY WITH EMPTY TABLE option has been activated after the last
integrity check on T, its parents, or its underlying tables
- The cascading effect of full processing, when any parent of T (or underlying table,
if T is a materialized query table or a staging table) has been checked for integrity
non-incrementally
- If the table was in check pending state before migration, full processing is required
the first time the table is checked for integrity after migration
- If the table space containing the table or its parent (or underlying table of a materialized query
table or a staging table) has been rolled forward to a point in time, and the table and its
parent (or underlying table if the table is a materialized query table or a staging table) reside
in different table spaces
- When T is a materialized query table, and a LOAD REPLACE or LOAD INSERT operation directly into T
has taken place after the last refresh"
But I really dont know what happened with my table.
Hope this help you out.
If you are familiar with Virtual Server you know that you can use it to run scripts on the Host OS by attaching them to events, such as: turning on or off the Virtual Server service, or turning on or off a virtual machine.
But these scripts run on the host. What if you want to launch an application inside the guest OS?
Suppose you have a VBScript file called MyVBScript.vbs, and you want to run it inside the guest operating system of a virtual machine, or a bunch of them. You can create an ISO image that will contain an Autorun configuration that will execute this script. Once that's done, you can simply attach the ISO file to the virtual machine(s) where you want your script to run.
We will use the unauthorized ISO Recorder Power Toy to create the ISO file. ISO Recorder v2.0 works on Windows XP and Windows 2003. After you install this application you will be able to create ISO files out of folders in your filesystem.
- Create a new folder. Let's call it VMScript.
- Copy MyVBScript.vbs to the VMScript folder.
- Create a new file in the folder called Autorun.inf.
- Edit the Autorun.inf file and add the following lines:
[autorun]
open=wscript MyVBScript.vbs
- You can replace the text after "open=" if you want to execute a different command line, you can even launch an application with a UI.
- Save the Autorun.inf file.
- Right clik on the VMScript folder and select Create ISO image file.
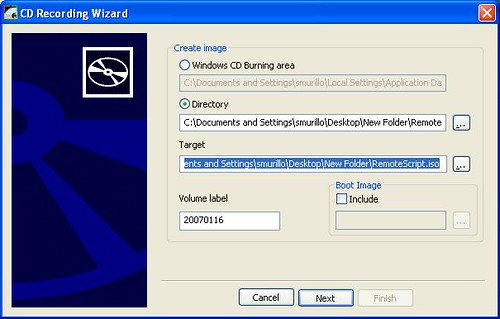
- Follow the wizard steps and a new file called RemoteScript.iso will be created. This is the CD/DVD image that you can attach to the virtual machine where you want the script to run. When you do, unless the Autorun feature has been disabled, your script will launch in the guest OS.
This is the same technique that Microsoft uses to launch the VM Additions and the precompactor. Now you can exploit this and even create interesting combinations. For instance you can attach a script to an event in Virtual Server that will attach your ISO file to a virtual machine.
IMPORTANT NOTES:
- ISO Recorder is meant to be used for personal use, but it is used by a number of companies around the world. I have found no problems with it. Make sure you read the license agreement and documentation for this application.
- AutoRun is normally enabled by default on Windows operating systems. For more information on this read CD AutoRun basics.
- If you are not that familiar with Virtual Server and you don't know how to attach ISO files, manage removable media or attach scripts to Virtual Server, read the Virtual Server Administrator's Guide included in the installation package.
Juan Pastor recently published an article that analyzes the risk of having mission critical applications running on non supported software (does it sound like VB6?). Will you get in trouble with Sarbanes-Oxley? Read on and you'll find out. However, let me just ask you this: Why should you take the risk?
-------
The white paper considers the latest developments regarding SOX compliance and explains how organizations can ensure ongoing certification by migrating their legacy finance applications to a modern IT platform.
Link to Migrating-Away-From-Compliance-Quicksand